Cloud security challenges are one of the reasons organizations are hesitant to use cloud computing. If not handled effectively, these issues can lead to data breaches, unauthorized access, service disruptions, and potential loss of sensitive information, undermining the trust and reliability that organizations and individuals place in cloud technologies.
The main problem with cloud security challenges is that many businesses fail to distinguish between the responsibilities of cloud service providers (CSPs) and their own, thus failing to implement the necessary cloud security measures.
According to the “2023 Cloud Security Challenges Report” by Cybersecurity Insiders, security is still a top concern for cloud users despite cloud computing’s fast uptake. %76 of the cybersecurity experts surveyed said they are at least somewhat concerned about public cloud security. This article delves into the complicated area of cloud security challenges. We’ll provide insight into how cyber attackers’ techniques are evolving, as well as the actions businesses must take to ensure their cloud systems are secure and reliable.
Top 11 Cloud Security Challenges
The “Top Threats to Cloud Computing: The Pandemic 11” report was issued in June by the Cloud Security Alliance (CSA). According to a working group of experts, including engineers, senior programmers, and management staff, there is a shift in cloud security from information security to configuration and authentication.
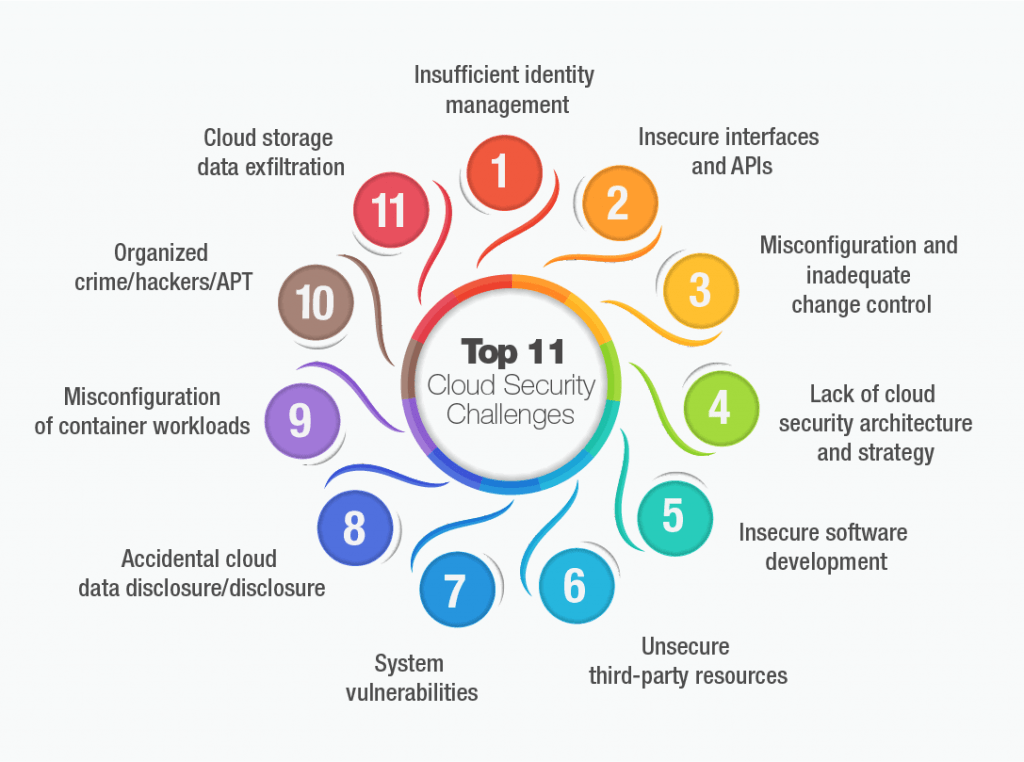
The Study reveals these 11 major cloud security challenges:
- Insufficient identity, credentials, access, and key management
- Insecure interfaces and APIs
- Misconfiguration and inadequate change control
- Lack of cloud security architecture and strategy
- Insecure software development
- Unsecure third-party resources
- System vulnerabilities
- Accidental cloud data disclosure/disclosure
- Misconfiguration and exploitation of serverless and container workloads
- Organized crime/hackers/APT
- Cloud storage data exfiltration
Security Challenge 1: Insufficient Identity, Credential, Access, and Key management, Privileged Accounts
Systems for managing identities, credentials, and access are called “Identity and Access Management”, shortly IAM. IAM lets organizations control, monitor, and secure access to important assets. Modern cloud breaches are largely caused by insufficient IAM and it comes in first place in the cloud security challenges list.
How Does It Affect The Business?
- Data displacement and malicious or unauthorized user exfiltration
- Financial costs associated with incident response and Loss of market income and trust
- Interruption of the supply chain
- Ransomware
A Real Life Cloud Security Challenge Sample
The majority of the attacks in 2021 were misuse of IAM tools, and they involved Twitch, Cosmology Kozmetik, PeopleGIS, Premier Diagnostics, SeniorAdvisor, Reindeer, and Twillo.
In 2021, there were breaches including Twitch, PeopleGIS, Premier Diagnostics, and Twillo, with the majority of these incidents abusing misuse of IAM tools.
How to Deal
Organizations should implement two-factor authentication, follow rigorous IAM cloud restrictions, cycle their API keys often, and delete unused credentials.
Security Challenge 2: Insecure Interfaces and APIs
The most common reason for incidents and data breaches is improperly configured Application Programming Interfaces (APIs), and user interfaces. Any cloud service’s security begins with how well these are protected, and both customers and cloud service providers are accountable for this.
How Does It Affect The Business?
The most common business impact is the exposure of sensitive or private data because it is not fully secured by the API. If a customer transaction API is unintentionally deployed without the necessary authentication and authorization checks, anyone using the API could view a lot of sensitive customer data.
Examples of This Security Challenge
In September 2018, Facebook announced that because of a vulnerability in the Facebook application programming interface (API) code for its View As feature, fifty (50 million users’ data were affected, and the access token for the API had been stolen*.
How to Deal?
- API keys must be kept private and never used again. Rely on widely used API frameworks that are security-conscious.
- Establish trusted identities and then use tokens associated with those identities to control access to services and resources.
- You can authenticate traffic using a reliable API gateway, and you can also manage and track API usage.
Security Challenge 3: Misconfiguration and Inadequate Change Control
Misconfiguration and inadequate change control come in third place on the cloud security challenges list.
Misconfigurations can be caused by a lack of system knowledge or a lack of awareness of security settings. Default configuration options and login credentials, unprotected secrets, and permissions that exceed the user’s authorization are among those errors.
How Does It Affect The Business?
There is even no need for a cyber attack, as misconfiguration can reveal passwords and keys. Excessive user permission causes greater application security risks.
A misconfigured database server could allow data to be accessed using a standard online search. If this data contains administrator passwords, an attacker will have access to data outside the database.
Examples of Cloud Security Challenges
In 2019, all NASA personnel’ identities and email addresses, their positions as allocated to projects posted on Jira, as well as ongoing NASA projects and impending milestones, were exposed as a result of these improperly configured global permissions schemes*.
How to Deal?
- The configuration of the prod, dev, and QA environments must be the same and automated, but each environment must utilize a different set of passwords
- To find any security configuration errors or missing updates, periodically scan and audit your infrastructure
- Review user permissions
Security Challenge 4: Lack of cloud security architecture and strategy
Organizations tend to rapidly move to the cloud to reap the benefits of cloud computing. However, they need to be aware of the risks they face and how to migrate safely to the cloud before making the switch. To have a safe cloud infrastructure, an appropriate cloud migration roadmap should be used.
How Does It Affect The Business?
Without a good cloud strategy plan, cloud infrastructures and apps might be vulnerable to cyberattacks.
Examples of Cloud Security Challenges
In 2021, online apparel store Bonobos had a significant data breach in which hackers stole 70GB of customer information by accessing a backup file on a cloud hosting network.
How to Deal
- Robust identification controls
- Automate the reactions to security events
- Protect the infrastructure at all levels
- Use data encryption
Security Challenge 5: Insecure Software Development
Insecure software development comes in fifth place in the cloud security challenges list. Developers avoid creating the infrastructure and/or platform layers from scratch by giving management of those layers to a cloud service provider.
Software Developers can concentrate on business logic by using services for Continuous Integration and Continuous Deployment. CI/CD is a DevOps practice that has become one of the best practices for software development to ship software quickly and efficiently.
Even though DevOps implementation unintended functionality might appear as a result of the complexity of software development, opening the door for the development of exploits.
How Does It Affect The Business?
Industries are increasingly “being operated on software and offered as online services,” from energy and healthcare to banking and communications. So developing insecure software has some consequences both financial and legal.
Real Life Example
In January 2021, four zero-day vulnerabilities in on-premises Microsoft Exchange Servers were found. These vulnerabilities gave attackers complete access to user emails and passwords on the vulnerable servers, administrator rights on the server, and access to connected devices on the same network. Attackers frequently set up a backdoor that gives them total access to the affected servers.
How to Deal?
- Focus on the CSPs’ guidelines on how to deploy services in a secure manner, such as a Well-Architected Framework or secure design patterns.
- By implementing the shared responsibility paradigm, some responsibilities can be owned by the CSP, rather than the business.
Security Challenge 6: Unsecure Third-party Resources
The exploit can start at any point in the chain and spread since a product or service is the culmination of all the other products and services it uses. This indicates that a hostile hacker “just” needs to hunt for the weakest connection as a point of entry in order to accomplish their objective. Using SaaS and open source to scale is standard practice in the software industry. The same opportunity for growth is given to malicious hackers, who can use the same exploit to harm more targets.
How Does It Affect The Business?
Key business operations and authorized access to business data are lost or stopped. A loss of income could result from any outcome.
Example of This Security Challenge
The breach in the supply chain that affected the SolarWinds Orion system in 2020 is referred to as the SolarWinds hack. Hackers gained access to SolarWinds’s customer IT systems, which they used to add more malware and spy on other businesses and organizations.
How to Deal?
- Determine and monitor the third parties you use.
- Review the external resources on a regular basis. Removing the items and revoking any access or rights you may have given them is a good idea if you discover products you don’t need.
- Use DAST and SAST. While DAST evaluates the operating program without having access to its source code, SAST scans the application code while it is at rest to look for flawed code that poses a security hazard.
Security Challenge 7: System Vulnerabilities
Some platforms may have defects called system vulnerabilities. They could be taken advantage of in an effort to jeopardize the security, integrity, and accessibility of data, potentially causing service operations to be disrupted.
How Does It Affect The Business?
Companies’ operations may be affected by a data breach, prohibiting clients from using the company’s services. If the company’s reputation and services are no longer trusted in the wake of a breach, it could be more difficult to attract new customers.
Examples of Security Challenges
2021, a remote-code vulnerability known as Log4Shell affects Java-based Log4j logging facility versions. Given the extensive use of Java in cloud systems, Log4Shell is a serious concern. By sending a malicious request to a weak system, an attacker can utilize Log4Shell to steal information, start a ransomware attack, or take over the system by making the system execute arbitrary code.
How to Deal?
- Using strong and unique credentials. Strong authentication credentials make it difficult for potential attackers to access system resources and related data.
- Deploying updates for known critical vulnerabilities as soon as they are made available decreases the attack surface of the system.
- System vulnerability-related security risks can be significantly reduced by following strict IAM procedures along with routine vulnerability detection and patch distribution.
Security Challenge 8: Accidental Cloud Data Disclosure
The management approach that enables effective and efficient security management and operations in the cloud environment is referred to as cloud security governance.
A lack of security governance and control is frequently caused by the complexity of the cloud and a move to cloud-service ownership with varied teams and business divisions.
How Does It Affect The Business?
Unexpected expenditures are incurred by data exposure, including those for forensic teams, customer support procedures, and compensation for impacted customers.
Examples of Cloud Security Challenges
In 2021, the free gaming website VIPGames.com exposed more than 23 million records on a server that was improperly configured.
How to Deal?
- Review the PaaS workloads for databases, storage, and computation.
- Implement least-privileged IAM policies.
- Identify the services that permit traffic to be exposed externally.
Security Challenge 9: Misconfiguration and Exploitation of Serverless and Container Workloads
The infrastructure and security measures needed to run applications are still difficult for development teams to scale and manage. Serverless and cloud-native workloads may appear to be the solution to this issue, shifting this burden to the cloud service provider (CSP). However, compared to moving virtual machines to the cloud, it necessitates a greater level of cloud and application security maturity.
How Does It Affect The Business?
Applications using serverless technology should be implemented carefully and expertly to avoid serious security breaches, data loss, and financial weariness.
Examples of Cloud Security Challenges
A DoW assault is comparable to a DoS attack. To affect the underlying infrastructure, the attacker bombards a serverless application with numerous requests.
However, the goal of a DoW attack is to defraud a cloud customer by exploiting the serverless platforms’ auto-scaling consumption paradigm.
How to Deal?
- Utilize tools for Static Application Security Testing (SAST) to incorporate code scanning into the CI/CD process.
- To prevent the secrets from being kept on disk or in environment variables, utilize a cloud key management service (KMS).
- Use API Gateways.
- Separate the staging, development, and production environments. This guarantees that appropriate vulnerability management is given the top priority at every step of development.
Security Challenge 10: Organized Crime/Hackers/APT
The phrase “organized crime” is used to indicate the degree of organization a group would have when producing deliberate acts that represent the efforts of group members. The phrase “advanced persistent threats” (APTs) refers to a broad category of attacks that an intruder or team of attackers launches.
How Does It Affect The Business?
The driving forces of those organizations can vary from one group to another. Some have political motivations, whereas others are a part of an organized crime gang.
Sample Cloud Security Challenge
The Bangladesh Bank cyber heist, often referred to as the Bangladesh Bank robbery, happened in 2016. A $1 billion heist on Bangladesh’s state bank was planned and almost carried out by hackers known as the Lazarus group.
How to Deal?
- To quickly identify and isolate any hostile events, implement detailed system monitoring.
- Educate your users on security.
Security Challenge 11: Cloud Storage Data Exfiltration
Cloud storage data exfiltration is the unauthorized transfer of data. Data exfiltration might happen accidentally or as a result of the acts of persons who are malicious or compromised.
How Does It Affect The Business?
There are various effects from regulatory responsibilities to warn to recompense people impacted besides losing the trust of consumers.
Example of This Cloud Security Challenge
Jean Patrice Delia stole more than 8,000 documents from General Electric (GE) over the course of eight years. Delia intended to use insider information to launch a competing business.
How to Deal?
- Train the employers about data breaches and data exfiltration.
- Using Encrypted data.
- Prepare an incident response plan.
Conclusion
As long as businesses keep records and store sensitive data, cyber threats including data loss and leakage, malware/ransomware attacks, phishing, and denial of service assaults will exist. To reduce the risks of cloud security, organizations must integrate security awareness and best practices into their culture. Also, a cloud consulting service may assist in creating policies in accordance with the organization to follow all requirements for cloud security challenges.
As more businesses move towards cloud computing, choosing the best cloud security consultancy service to handle emerging cyber security threats has become critical. Nioyatech provides independent cloud consulting and solutions for businesses. As professionals and experts working in cloud consulting, Nioyatech can assist you create a guide to the best cloud benefits for your business
*Sources:
Insecure Application Programming Interfaces (APIs) in Zero-Trust Networks by Farhan A. Qazi